
This one, it’s slightly lower
on the Hard Level scale than the last,
so perhaps that’s why
it feels like it’s coming together
a bit more quickly.( ´∀`)

Screenshot 1.
Right, so my own rather
literal translation of
the question is as follows:
is as follows.
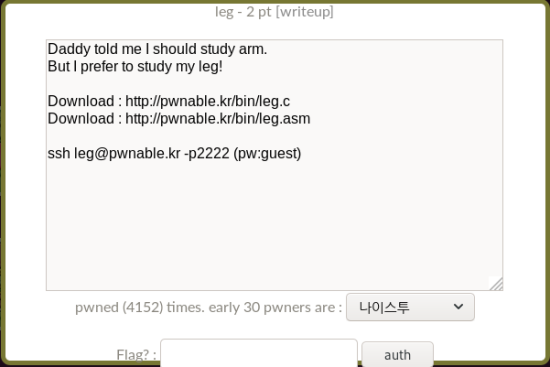
Daddy told me I should study arm.
But I prefer to study my leg!
Screenshot 2.
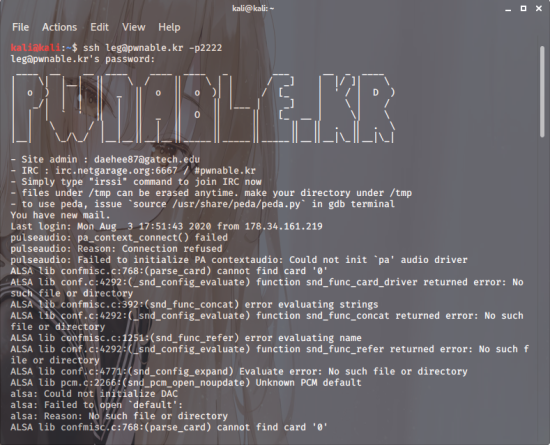
1 | ssh leg@pwnable.kr -p2222 |
You just connect straight away.
Screenshot 3.
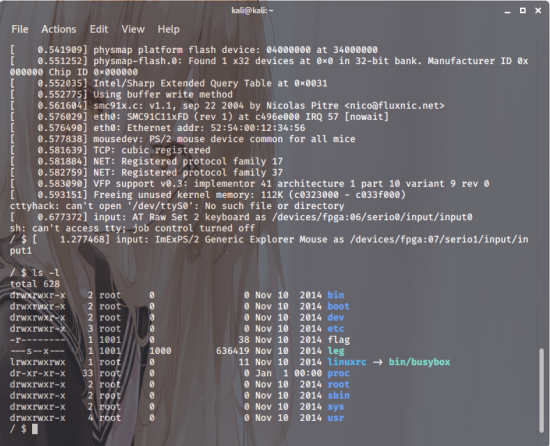
First, you verify the files with ls -l
But there doesn’t seem to be a way to do it,
the access attempt just isn’t working…? ōxō
the access attempt just isn’t working…? ōxō
Right, then let’s look at
the download section that was in
the question earlier:
that was in the question earlier.
Download :
http://pwnable.kr/bin/leg.c
http://pwnable.kr/bin/leg.asm
You download them both.
Once downloaded, let’s immediately
check leg.c.
Screenshot 4.
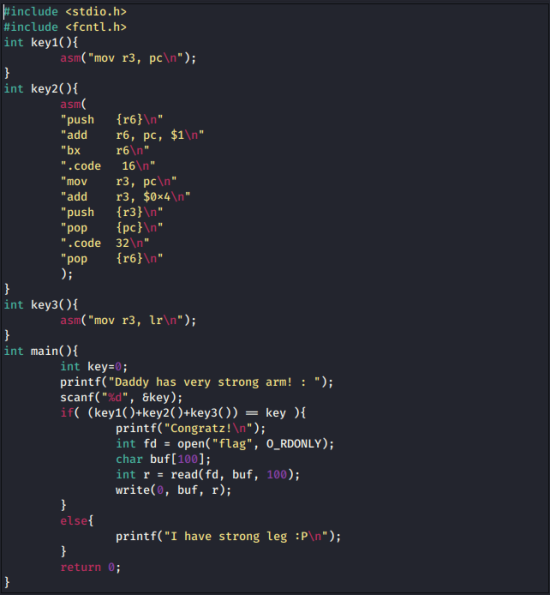
The functions for key1 through 3
are written in ARM assembly.
are written.
First, if you look at the main function,
it seems that if you match the value
that’s the sum of all three of those
function values,
you can snag the key value.
if you match the value that’s
the sum of all three of those function values,
you can snag the key value.
Let’s have a look at the main function’s
assembly code as well.
as well.
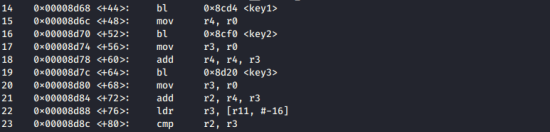
It’s evident that the r0 values obtained
through the functions are all summed up,
and the final result goes into r2.
are all summed up,
and the final result goes into r2
it’s evident
then, let’s look at each function.

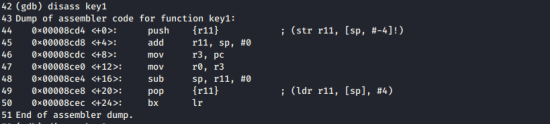
Screenshot 6.
This is the C and assembly code for the key1 function.
It puts the pc value into r3
and then puts r3 into r0 again.
So, the pc value will then be the value for key1
will then be the value
If we just take a quick look at what pc is:
Right, so when a CPU executes a
single instruction,
it’s said to go through
the fetch, decode, and execute stages.To execute two opcodes,
you’d then need a total of six operations:
fetch, decode, execute, fetch, decode, execute.By performing these stages in
parallel, however, you can reduce those
six operations needed for two opcodes
down to just four.It’s simply more efficient than doing it
sequentially, you see.
The Program Counter,or PC,
holds the address for the fetch operation.If the current instruction is at
the execute stage,
the next one will be at the decode stage,
and the one after that will
then be at the fetch stage.Consequently,
the PC will then hold the address of
the instruction that’s
due for the next fetch operation.
Right, back to the main point now.
The pc value in the key1 function is
0x00008ce4
is.
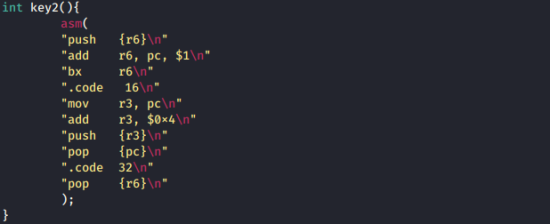
Now, let’s move on to key2.
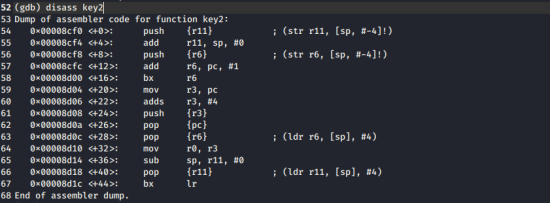
Screenshot 7.
You assign the pc value(0x00008d08)
to r3, and then add 4,assigning that to r0
assigning that to r0
The value of key2 is
0x8d08 + 4 = 0x8d0c
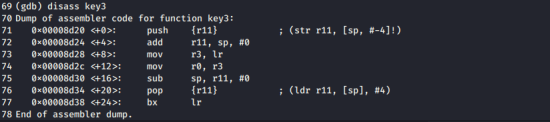
Let’s look at key3.

Screenshot 8.
You assign the lr value to r3
and then assign the r3 value to r0
So, I suppose one just needs to find the lr value.
one just needs to find it.
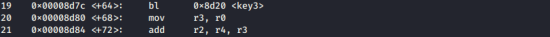
If you look at the main function:
Screenshot 9.
The lr value is
0x00008d80
All three values have now been obtained
key1 | 0x8ce4
key2 | 0x8d0c
key3 | 0x8d80
If you sum them all up,
0x1a770
Right, then let’s go snag that key value
immediately, eh?
let’s go snag it ㅋㅅㅋ
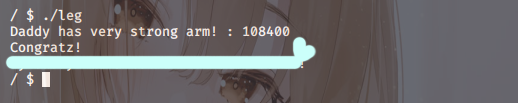
So, into the input window here
I’ll input 108400.
And due to the program’s nature
it absolutely must be entered
as an integer.
Screenshot 10.
And so the key value comes out
Screenshot 11.
With the value that’s been snagged,
you go back to the first screen,
input it into the blank space,
and then just press the ‘auth’ button.
As soon as the mission is completed,
2 points have been snagged.
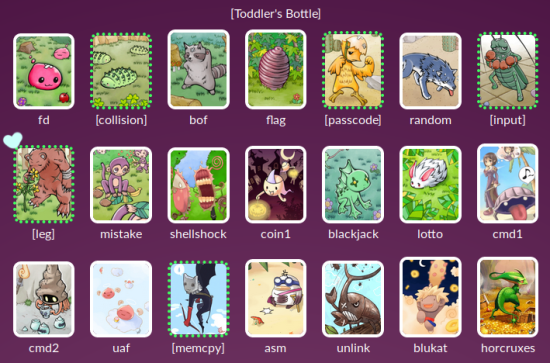
then, if you go back to the initial screen again,
you’ll see that
it’s marked as completed with a green
dotted line
Thanks for reading through this long post.
Well done. (ㆁᴗㆁ✿)
Have a good day, and
I hope everything works out well for you,
It’s quite warm out,
so do try and avoid getting heatstroke
And do take care with the,erm,
Wuhan pneumonia situation.

