The difficulty is quite substantial,ōxō
The difficulty is quite substantial,ōxō
In the case of exploits
I referred to someone else’s exploit code externally
I referred to it.
It seems to be socket programming
and it’s as if I need
to refer to some old socket programming books
lying around at home.
old socket programming books.
I need to refer to them.

Kim Jong-sung
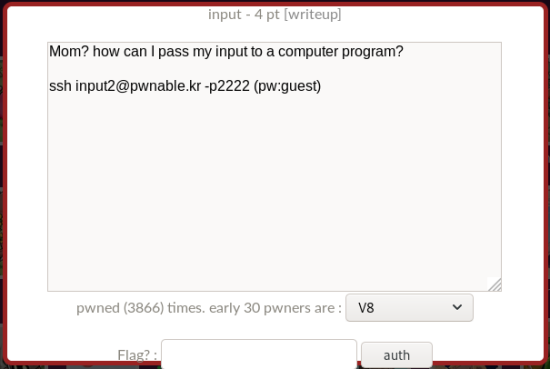
Screenshot 1.
Again, with my straightforward, literal translation, the question is as follows:
Mom? how can I pass my input to a computer program?
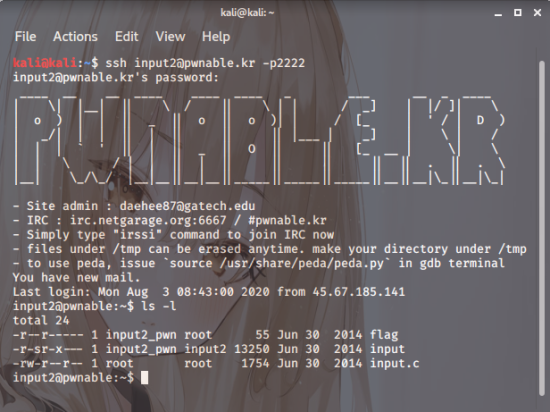
Screenshot.2
Right, then I’ll try connecting straight away.
1 | ssh input2@pwnable.kr -p2222 (pw:guest) |
And if I type ls again, you’ll see
a total of 3 files appear.
And then,
with the cat command,
input.c
I’ll check it.
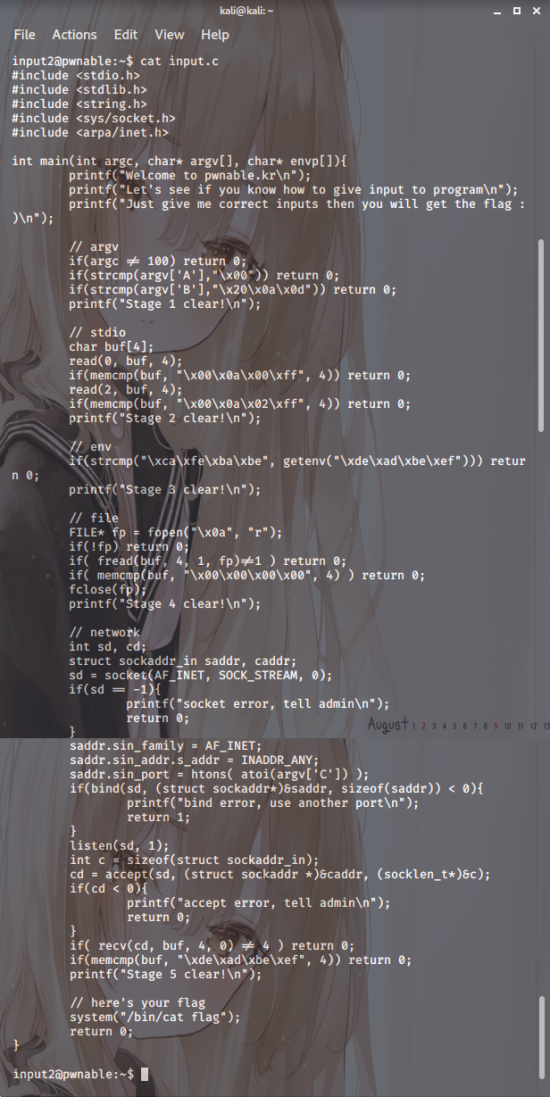
Screenshot.3
Ba ha ha ha ha ha ha
This source code, you see,
is rather long, ōxō.
is rather long, ōxō.
Looking at it overall,
let’s consider the conditions
for passing Stage 1.
let’s consider the conditions for passing.
: )
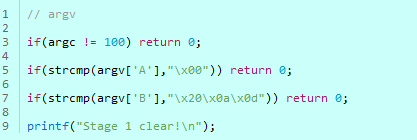
Code.1
1. Number of arguments = 100
2. argv[‘A’] = \x00
3. argv[‘B’] = \x20\x0a\x0d
If that’s the case, Stage 1 will be completed.
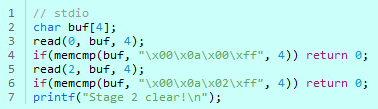
Code.2
It’s Stage 2
You provide \x00\x0a\x00\xff as stdin input
you provide input,
sterr,
you must give\\x00\\x0a\\x02\\xff
for it to be completed.
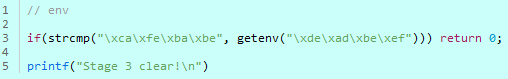
Code.3
stage 3.
It’s an environment variable.
You simply insert the value\\xde\\xad\\xbe\\xef be into the environment variable called
into the environment variable.
\\xca\\xfe\\xba\\xbe
you simply insert the value.
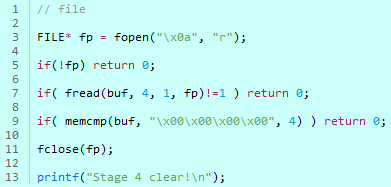
Code.4
It’s Stage 4
You open the file called \\x0a
and the first 4 bytes that are read
\\x00\\x00\\x00\\x00
for it to be completed.
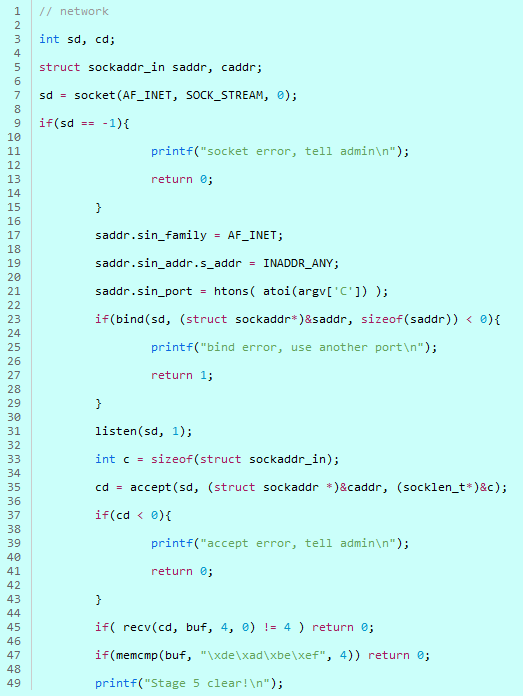
Code.5
It’s Stage 5
atoi(argv\[‘C’\]) = argv\[‘C’\]
The value converted to an integer
as the port number,
you open a socket server,
\\xde\\xad\\xbe\\xef
and if you send it,
Stage 5 will be completed.
Right, then I’ll attempt the exploit.
My skills aren’t quite up to
writing it myself just yet,
so I’ll be referring to exploit code
so I’ll be referring to it.
It’s written in Python, you see.
it’s written.
1 | from pwn import * |
Code 6.
However, this code, in the current directory,
can’t be used, you see.
Due to a lack of permissions…。
So, that’s why they say you need to use /tmp
which has the necessary permissions.
Right, so from /tmp
let’s proceed.
Oh, and before, I almost forgot to
take a screenshot, you see.
If you just run it straight,
it’ll say the flag file
isn’t there,
and the flag won’t show up.
1 | ln -s /home/input2/flag flag |
So, you have to add a symbolic link like this,
and then give it a go.
then, if you leave the symbolic link in place
and proceed,
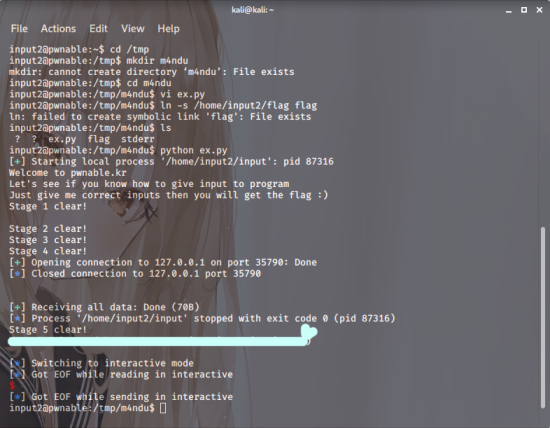
Screenshot.4
A short while later, that mint-coloured bit
that’s the key value, then.
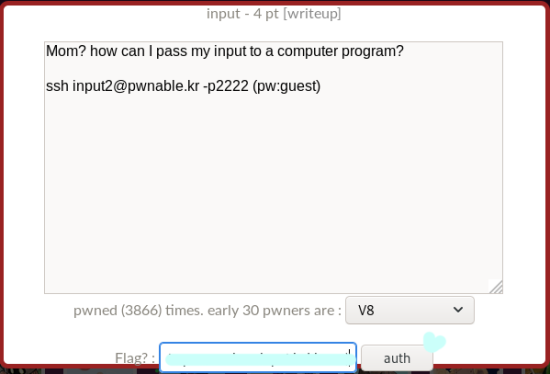
With the key value thus acquired
Screenshot.5
you go back to the first screen,
input it into the blank space,
and then just press the ‘auth’ button.
And as soon as the mission’s completed,
you snag 4 points.

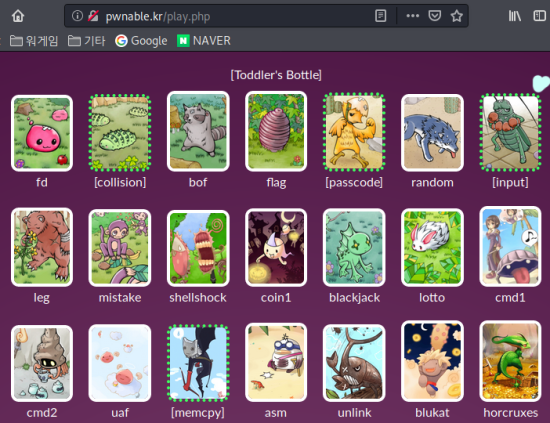
And if you come back, you’ll see it’s marked
with a green dotted line, meaning it’s been solved.
it’s been marked.
Thanks for sticking through this long post.
Well done, then. : )

Have a good day, and
I hope everything works out well for you
It’s quite warm out,
so do try and avoid getting heatstroke
and do take care with
the erm, Wuhan pneumonia situation : )