
Right, this one’s comparatively not too bad
difficulty-wise, you see
Right, anyway
due to my own circumstances,
I suppose
this study-related post
will have to be the last of its kind for now
I should really try a
bug bounty this year,
at the very latest.
The situation shows no sign of
improving, honestly.
ε-(´・`)
Honestly, rather than wasting all
my time and health with some
unwanted weekday part-time work,
with some unwanted weekday part-time work,
it’d be far less galling to do
bug bounties on weekdays
and just part-time work on weekends.
it’d be far less galling.
-`д´-
Right, anyway I’ll just carry on writing.
(ㆁᴗㆁ✿)

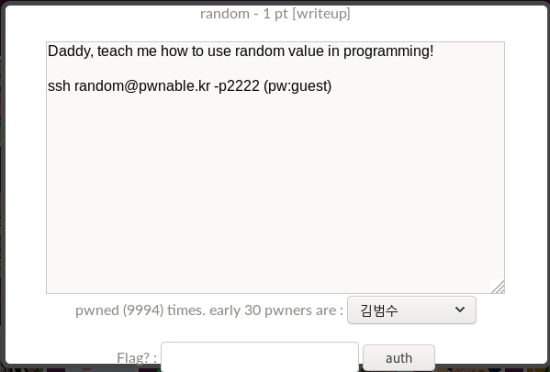
Right, first let’s have a gander at the question,
with my own rather straightforward,
literal translation
Daddy, teach me how to use random value in programming!
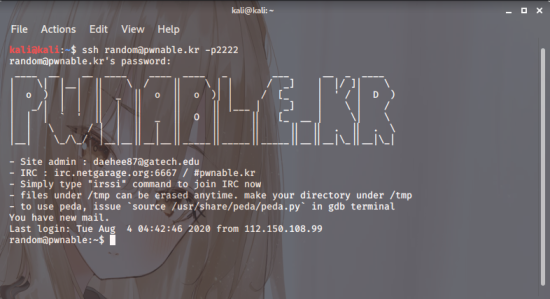
Right, and then
1 | ssh random@pwnable.kr -p2222 |
you connect straight away.
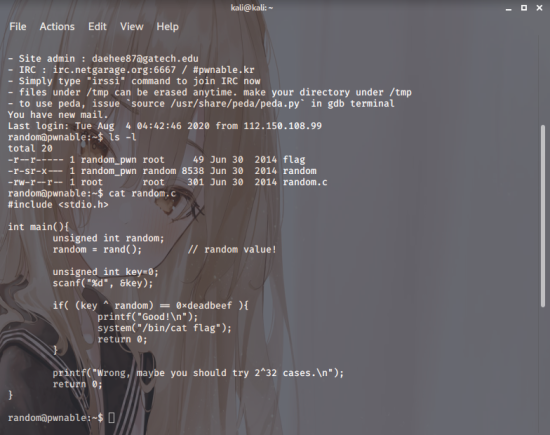
First,you work out whether
the file exists,and then
you check the random.c file
I check it
Right, so it’s a program that receives a
key value if you XOR a 4-byte
random value with an input value
if you XOR a 4-byte random value with an input value
and 0xdeadbeef comes out.
So, ANG? If it’s a random value,
does one have to try all possible cases?
Does one have to try all possible cases? ōxō
Does one have to try all possible cases? ōxō
one might think, but
the rand() function, unless
you provide it with a
seed value that changes every time
will always convert to a constant value
This constant value, if you work it out,
will give you the answer.
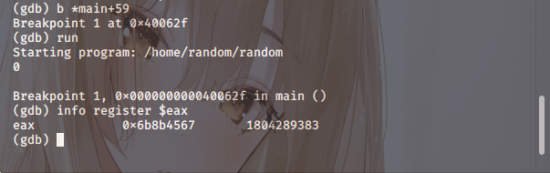
Right, then, let’s trace the value using gdb.
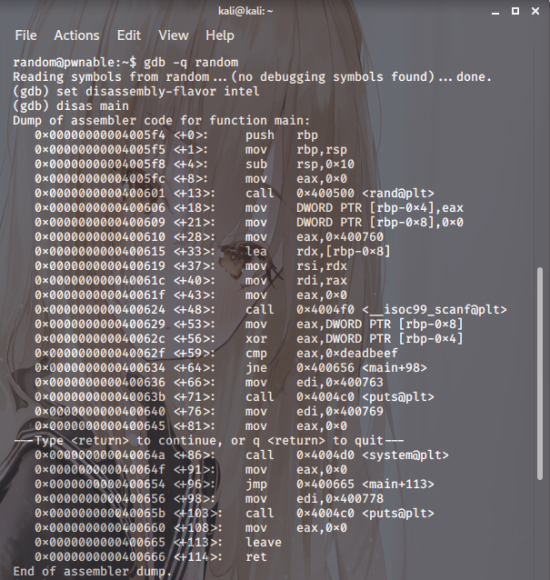
Right, so you do the XOR operation,
and it seems you just need to check
the value of eax 0xdeadbeef
you just need to check.
Screenshot 5.
If you set a breakpoint and run it, putting in 0
you can see that 0x6b8b4567 is in eax.
0x6b8b4567 is in eax
you can see that it’s in there.
As XORing with 0 produces the same value,
you can deduce that the value of rand() is 0x6b8b4567
you can deduce that it is.
So, the value we need to input can be found through
0xdeadbeef ^ 0x6b8b4567
can be found
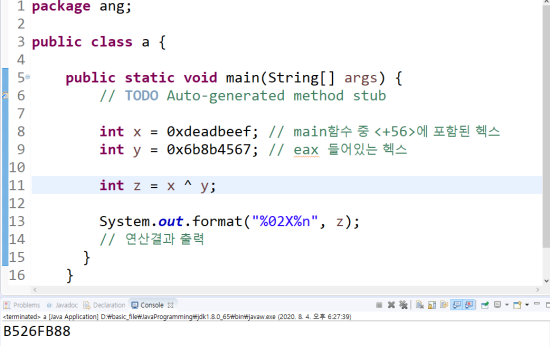
Screenshot 6: Hexadecimal operation in Java
If you operate these two using Java programming
if you operate these two
the result is
0xB526FB88
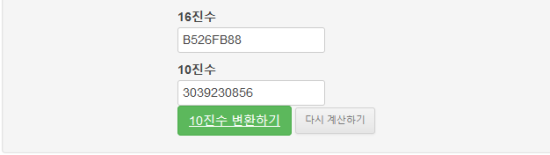
Screenshot 7.
And if you go to a conversion website and convert it,
3039230856
a value like the above is output
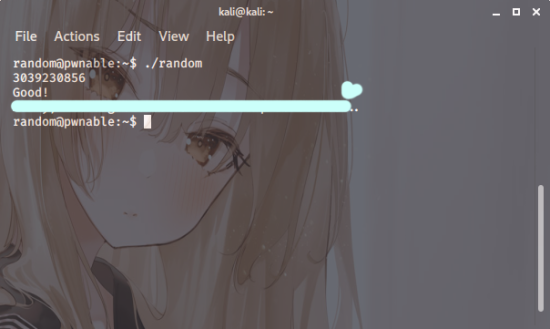
If you input the outputted value,
you acquire the key value like this.
Right, and then with the key value that’s
been snagged,
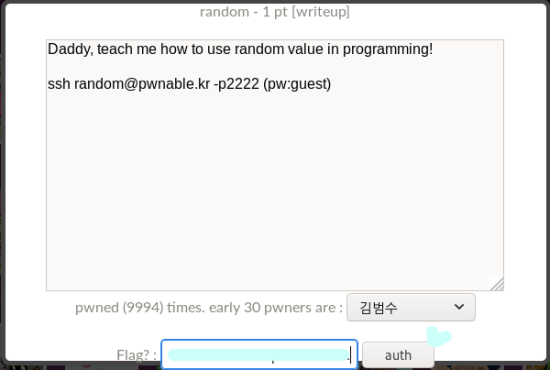
Screenshot 9.
you go back to the first screen,
input it into the blank space
and then just press the ‘auth’ button.
As soon as the mission’s completed,
1 point has been snagged.
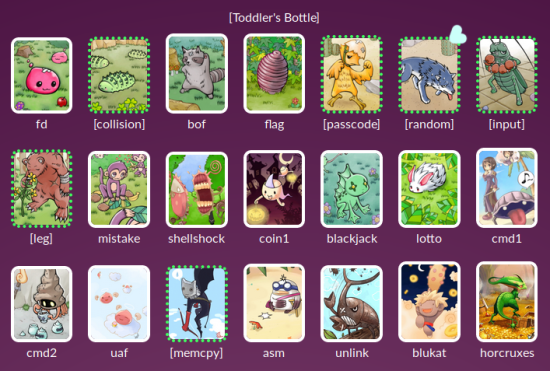
then, if you go back to the initial screen again,
you’ll see that
it’s marked as completed with a green
dotted line.
Thanks for reading through this long post.
Well done. (ㆁᴗㆁ✿)
Have a good day, and
I hope everything works out well for you
It’s quite warm out,
so do try and avoid getting heatstroke,
And do take care with the,erm,
Wuhan pneumonia situation.

