back on the 10th of April, 2022
Right, so this post was penned on a Naver blog.
https://blog.naver.com/bnm0170/222696804662

Right, well this is perhaps one of
the easier problems I’ve tackled so far.
Having a go at a CTF for ethical hacking
after a bit of a break, then.

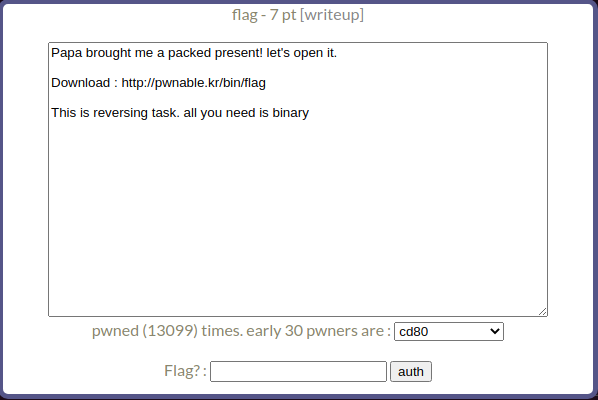
First off,let’s have a look at the question itself.
Papa brought me a packed present! let’s open it,
This problem, you see,
isn’t about SSH access.
Rather, it’s about downloading a
standalone program,
reversing it to get a key,
and then collecting points with that key.
Quite straightforward.
Right, anyway using
the download address written
in the question above,
you download it with the command below.
1 | sudo wget http://pwnable.kr/bin/flag |
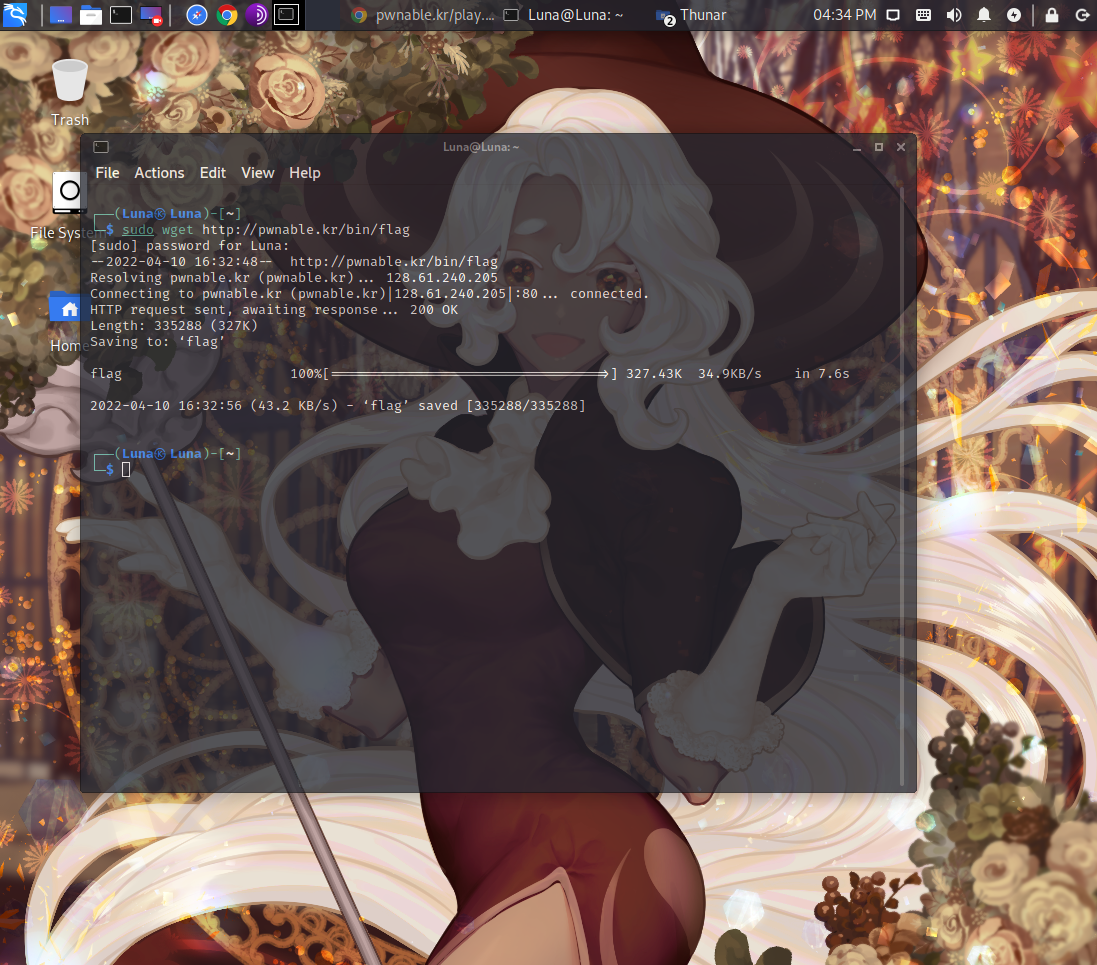
Once it’s all downloaded,
you then use the command below
to grant permission for the program to be used.
1 | sudo chmod 755 flag |
However,this program happens to be UPX-packed,
so you’ll need to unpack it as well.
Right, let’s go unpack it with the command below.
unpack it : )
1 | sudo upx -d flag |
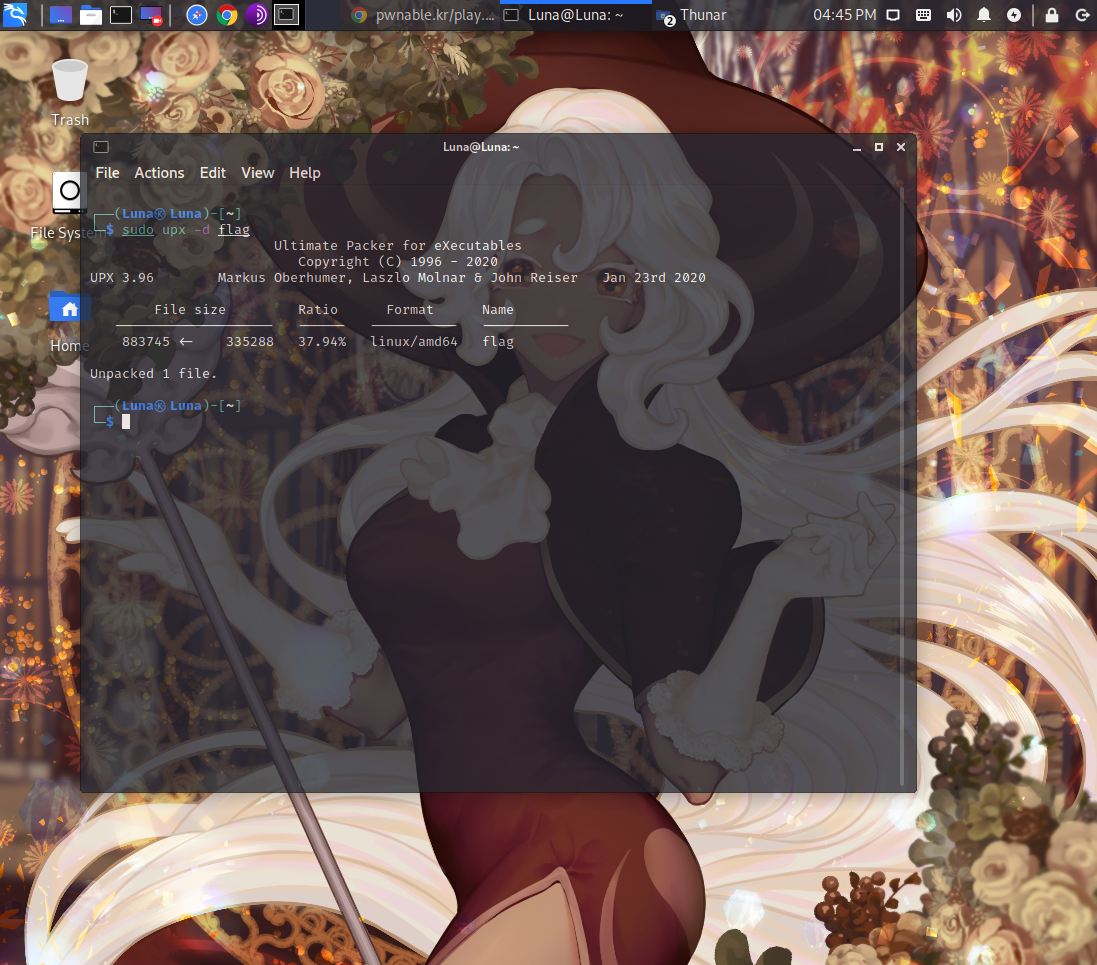
Now that the unpacking is complete, this time,
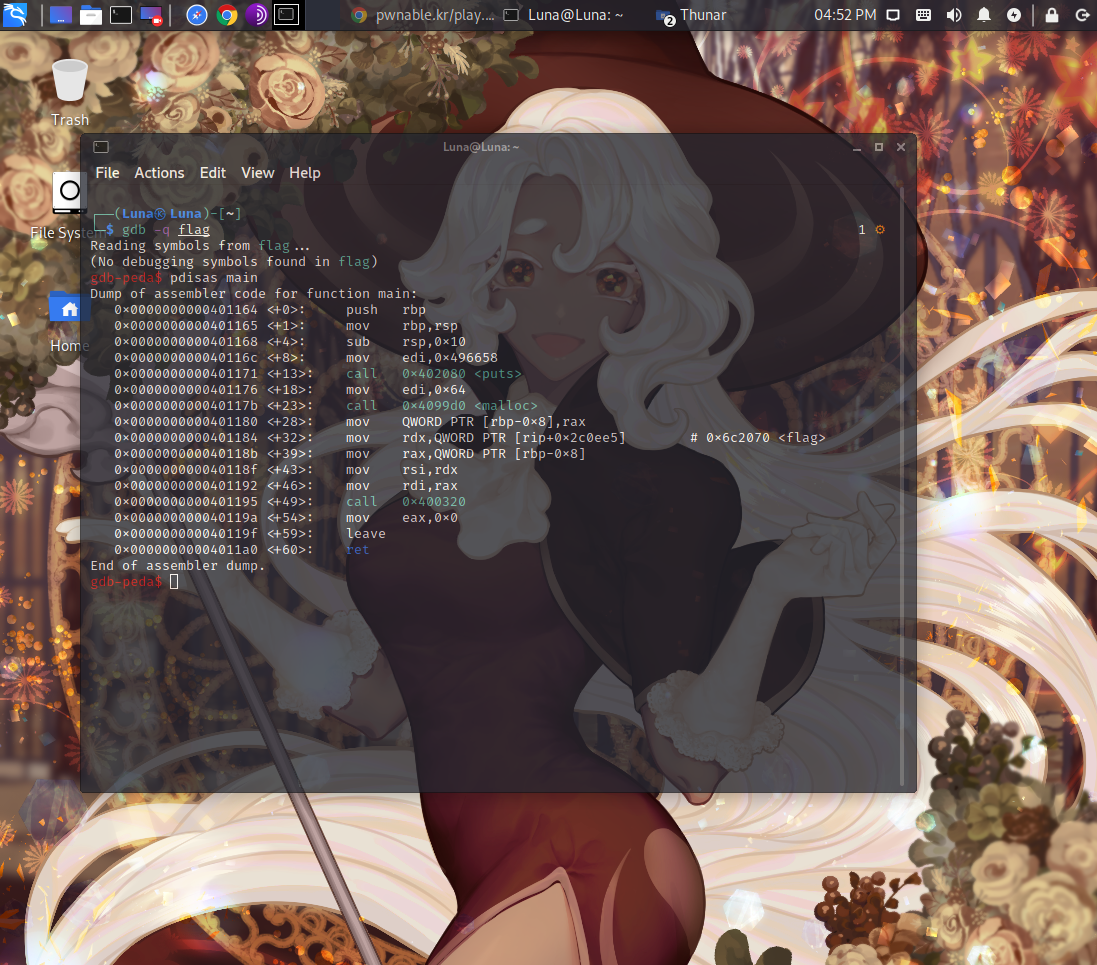
let’s try debugging it with the command below.
1 | sudo gdb -q flag |
(And in the meantime,
I completely wasted over
30 minutes trying to install gdb-peda,
you see.)
So, when you debug it in this manner,
after main+32,
there’s a rather suspicious part,
where it seems the flag value was copied to #
where there’s a rather suspicious part.
It’s presumed to be 64-bit, and
“if you disassemble 0x6c2070 with x/xg,
it comes out as
So, 0x496628 is probably where the real flag value
is copied to, I’d imagine.
Oh, and if you write 496628,
an error will be displayed,
so you absolutely must attach 0x,
and then write it. Otherwise,
it won’t be output correctly without an error.
it will be output.
Anyway, if you input it as per
the command below with x/s
if you input it.
1 | gdb-peda$ x/s 0x496628 |
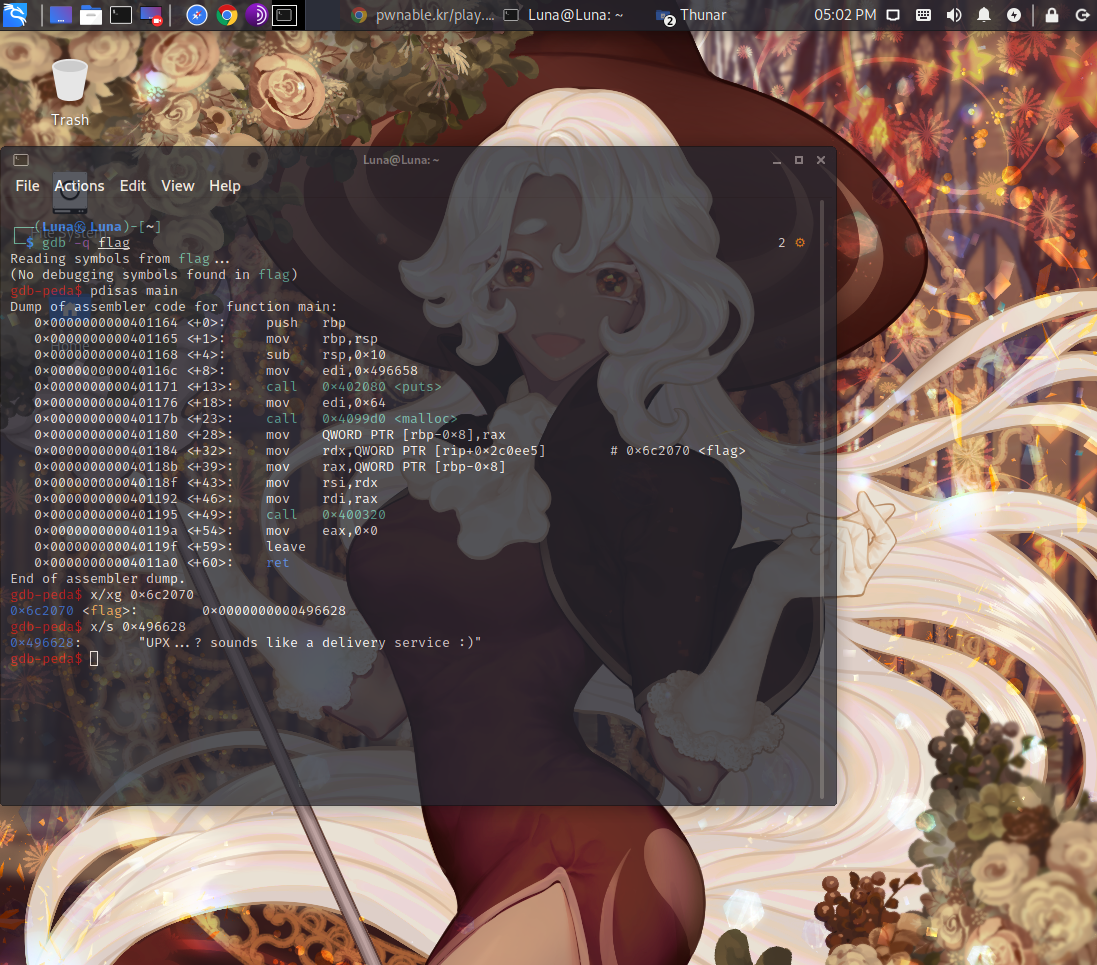
the real flag value will come out.
And with the flag value obtained,
you input the value as shown
in the captured image below.
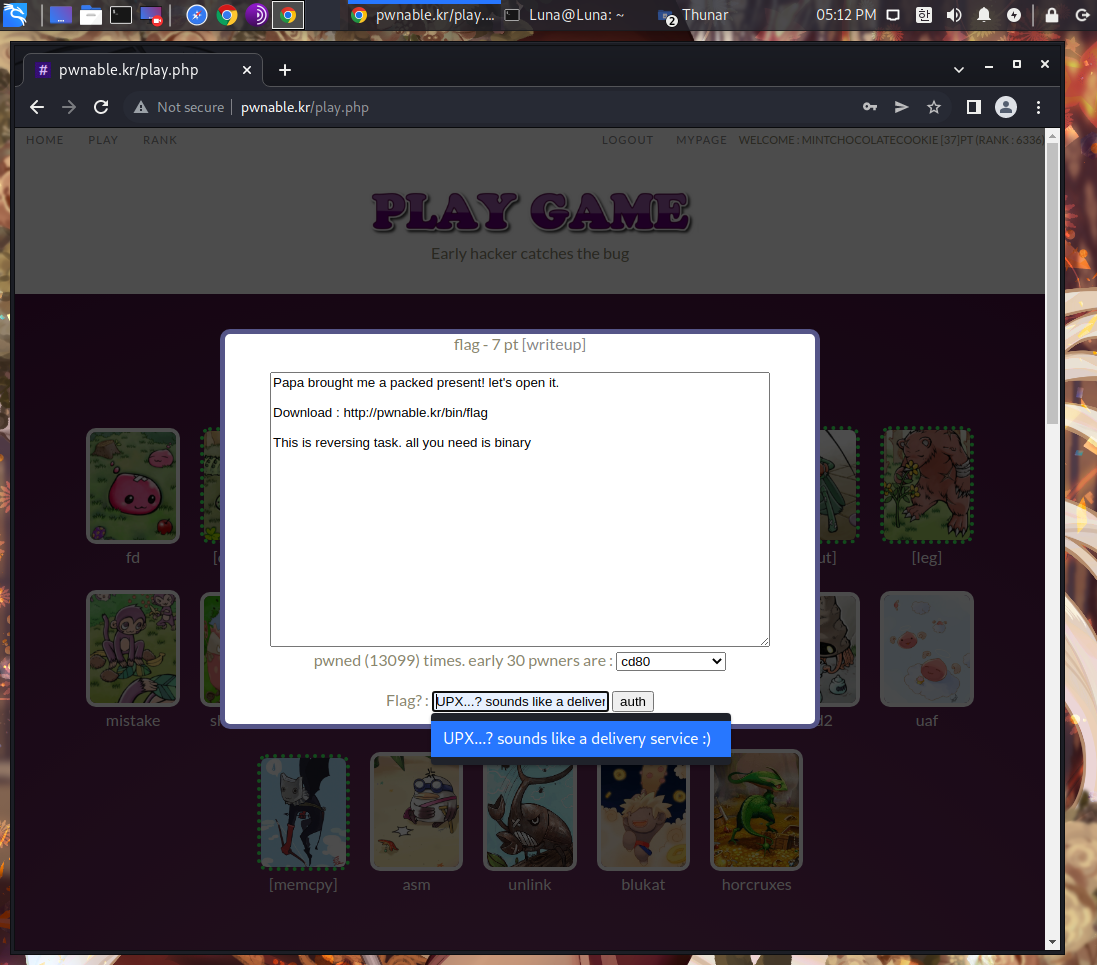

And that’s how 7 points were collected. : )

Having a go at pwnable.kr
CTF after a bit of a break, then.
“I’m not sure if it’ll
be possible since it’s
the weekend, honestly.
Right, well I suppose it’s about time
I started preparing for
some rather pointless part-time work.
My chances of finding employment in S.Korea(?)
are effectively long gone, you see.
So, while I’m doing short-term part-time work,
I’ll try to save up around ten million won,
move out of my family home,
and then find some temporary
accommodation near
the Japanese Cultural Centre,
in a well-soundproofed goshiwon.
and then find some temporary accommodation.
Ethical hacking, Japanese study,
preparing for JLPT N series or EJU,
bug bounty programmes related to ethical hacking,
preparing for and attempting that,
and then writing bug hunting reports
in English and Japanese,
writing bug hunting reports.
or preparing for OSCP,
an international ethical hacking
certification.
It’ll be like doing a penitent task,
just like the nuns in a Catholic convent.
I’ll have to do that.
And then, simultaneously with
preparing to move to Japan,
I’ll have to prepare for
financial income investment as well
2022.04.10